When you come across this error "LDAP Error: Connect error: TLS error -8054:You are attempting to import a cert with the same issuer" enrolling a client to FreeIPA/IDM server, it means that the existing certificate does not match the one...


When you come across this error "LDAP Error: Connect error: TLS error -8054:You are attempting to import a cert with the same issuer" enrolling a client to FreeIPA/IDM server, it means that the existing certificate does not match the one...

It's now possible to install both Puppet Master and Agent on the same host with different certs for each, to avoid future conflicts when managing master server with puppet. You need to have 2 seperate entries on puppet.conf, one in...

This article shows you how to Automate iptables for the whole infrastructure (linux/unix) and maintain the state during the lifecycle of a host. We would need to install 2 modules from PuppetLabs so that we can assign Rules based on the...

When adding multiple users in IDM/freeIPA its a pain inputting each user and its time consuming. This script/one liner allows you to enter multiple users at one go and it includes non-interactively specifying a password. The following...

This article covers the setup and configuration of PuppetDB and Puppetmaster on separate nodes/hosts. I have used PostgreSQL as PuppetDB backend instead of HSQLDB as it's much easier to query and troubleshoot any issues you comes across...

It's possible to get a list of users of active users in IDM/IPA with formatted date and time by running this one liner command. It gets you the list of users with last successsful authentications to IDM/IPA server. Very handy command when...
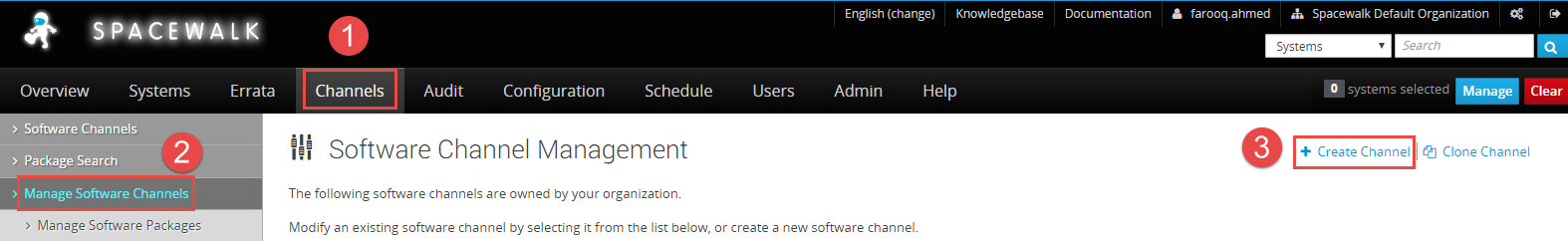
It's very easy to create a Kickstart tree in Spacewalk and that to in a Automated fashion for provisioning hosts. All you have to do is create a Base Channel for CentOS and then create a Repo and then marry both and then at the time of...

Its possible to configure Puppetdb with PostgreSQL as its much more manageable as compared to the in-built DB that comes with Puppetdb i.e. HSQLDB. Plus its much easier to query and troubleshoot any issues you comes across especially when...

It’s easy to setup Puppet server and a client in CentOS and RHEL by following the easy-to-follow steps given in this guide. You will need ROOT access for the install and setup. Pre-requisites (minimal): Hardware & Software CPU: 2 vCPU...

It is possible to automatically get a Kerberos Ticket (kinit) generated everytime you login via SSH to a host by editing ".bash_profile". This also applies to a scenario wherin you are using Red Hat IDM/IPA and want to automate "kinit"...
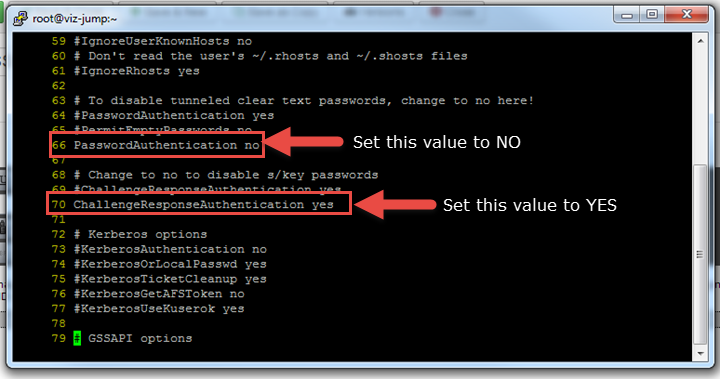
When using IPA for managing user authentication you can come across this issue of SSH dropping just after a password change. It can be resolved by changing options in /etc/ssh/sshd_config. You need to be ROOT to make this change and...
This article shows you the steps to install Spacewalk 2.2 (aka Satellite) version on CentOS. To start with the install we need make sure that firewall and hostname and IP are configured correctly. Make sure that these ports are opened in...

There might be a need to Change SUDO LDAP password whilst managing the SUDO rights centrally through IDM. In this scenario it would be the 1st time you are configuring the SUDO rights. Follow the steps outlined to change the password for...
This article shows you How To register Spacewalk Clients to the Spacewalk Server. All you need is to make sure before the registration you are logged in as ROOT and the SSL Cert is downloaded from the server to the client host. There is a...