It’s now possible to integrate FreeIPA/IDM (Red Hat) into vCenter Appliance (vCSA)/ vCenter Server for User authentications. We need to configure IPA server and vCenter Server for LDAP to authenticate users from IDM server. Follow this guide and you will up and running in no time with a fully working vCenter appliance/server with user authenticating from IPA Server. No need for Windows AD anymore 🙂 .
For setting up centralized authentication through IPA we would need to configure 2 things.
- IPA Server — Create a SSO Usergroup for vCenter Server and add it as a hosts, create object class.
- vCenter Server – Configure vCenter Server to connect and authenticate via LDAP to IPA Server.
Assuming that you have setup a fully working instance of the below.
- Working vCenter Appliance\vCenter Server.
- Working IPA Server/Red Hat IDM Server.
Configure FreeIPA/IDM Server
See the same via Video on YouTube!!
First need to configure IPA Server for SSO authentication.
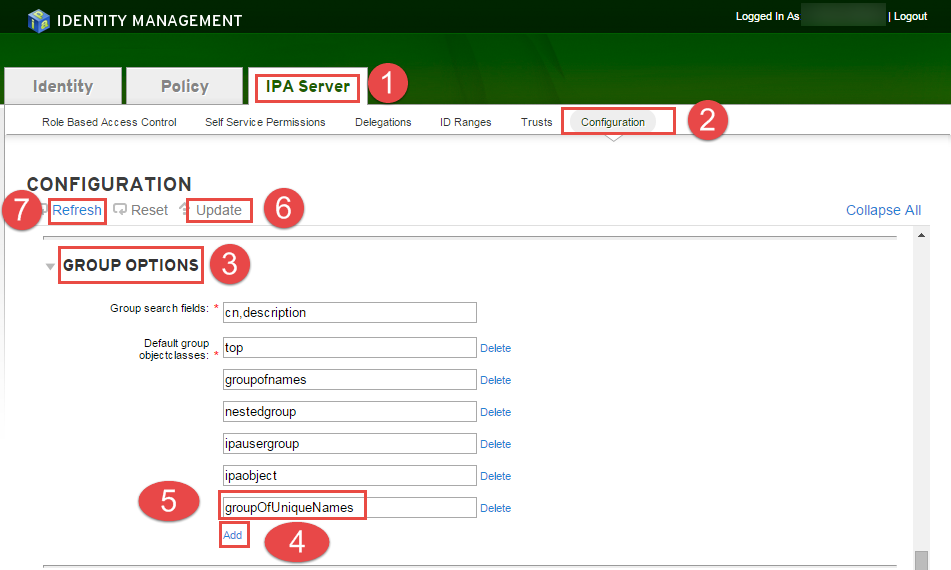
You need to add a object class in Group Options of IPA Server
Login to IPA WEBUI –> browse –> IPA Server –> Configuration –> Group Options –> Add –> GroupOfUniqueNames –> Update –> Refresh

Add a usergroup for SSO.
Goto –> IPA WEBUI –> Identity –> User Groups –> Add
- Group name : ssogroups
- Description : vCenter full access groups
- Group Type: POSIX

Now add a admin user for SSO group just created.
Goto –> IPA WEBUI –> Identity –> User Groups –> Add

Add users to the newly created SSO group
Goto –> IPA WEBUI –> Identity –> User Groups –> Add


Now add vCenter Appliance host IP & Domain Name to HOST list
Goto –> IPA WEBUI –> Identity –> User Groups –> Add

Now for the SSOGroup to work in vCenter its a requirement to run the below command. If you don’t then the users in the SSO group wont be able to access and you need to add inidividual users for granting access to vCSA.
# ipa group-mod ssogroups --addattr="uniqueMember=uid=user1,cn=users,cn=accounts,dc=dev,dc=local"where said user1 ==> change for the users in the group
If you get this error as given above, please type the following command to renew your Kerberos Ticket.
ipa ERROR: did not receive Kerberos credentials
# kinit adminNow you are done with the IDM part, lets start off with configuring vCenter now.
Configure vCenter Server Appliance for SSO authentication via FreeIPA/IDM Server
Next step would be to add the IPA server as Identity source in vCenter Server Appliance.
Login to vCenter Server Appliance using local/default login credentials via WEBUI at https://vcenter-server-6/vsphere-client (the link is for vCSA 6 and above. The link changes of vCenter version 5.x)

Then Goto Home –> Administration

Goto Configuration –> “+” sign to add the Identity LDAP Source with the following config as appropraite.

Select Identity Source Type: Open LDAP
Name: IPA
Base DN for users: cn=users,cn=accounts,dc=dev,dc=local
Domain Name: dev.local
Domain alias: Leave it Blank
Base DN for groups: cn=groups,cn=accounts,dc=dev,dc=local
Primary Server URL: ldaps://idm.dev.local:636
Secondary Server URL: ldaps://idmr.dev.local: 636
Username: uid=admin,cn=users,cn=accounts,dc=dev,dc=local
Password: This would be the admin user account for IPA/IDM Server

Make sure that you selcet the newly add DOMAIN as “Default Domain” so that you can login without @domain.local


To verify that the identity source is connected and working you should be able to see the SSOgroup users populated from IPA server as in below screenshot by browsing to Users & Groups –> Users.

Then add the SSOgroup to the required vCenter cluster you would like to have access to.
Goto –> vCenter Inventory Lists –> Resources –> vCenter Server –> Select the vCenter Server –> Manage –> Permissions



Add the ssogroups –> Add –> Domain “DEV.LOCAL” –> Select the ssogroups –> Add –> OK


Select the appropriate “Assigned Role” and the check on “Propogate to children” –> OK

Now logout and login back with the IPA login credentials and it should work and show you similar screens as given below.


The same you can check via vSphere Client and should be similar as given in below screenshots



We are all done now!! All the authentications should now work via IPA/IDM server. If Any issues please let us know via Contact Us and we would try our best to help.